What is a Threat Intelligence Platform?
Threat Intelligence Platform allows users to store and manage the threat database using various systems and resources such as security management applications such as, firewall APIs, and intrusion prevention systems. It analyzes the organization’s data on the repository of known threats by analyzing potentially active threats. Threat intelligence is a tool used by security researchers. When an assessment finds a risk, tools alert all security teams on this threat. It may result in greater accuracy for inaccurate numbers, but it is far more efficient than manually monitoring security data.
Threat intelligence platforms provide a critical source of intelligence that analyzes information for the identification, mitigation, and remediation of security issues. TIP is a web application that provides security intelligence to cybercriminals from companies worldwide through the use of threat intelligence feed tools for monitoring malware, domain names, files hashes and other information. TIP makes advanced analytics possible using real-time security data analysis for detection.
Advantages of a Threat Intelligence Platform
List of Threat Intelligence Platforms?
When you start looking for the best threat intelligence software, it is easy to get overwhelmed with the list of options available. Here is the handpicked list of threat intelligence software to choose as per your requirement:
1. ESET
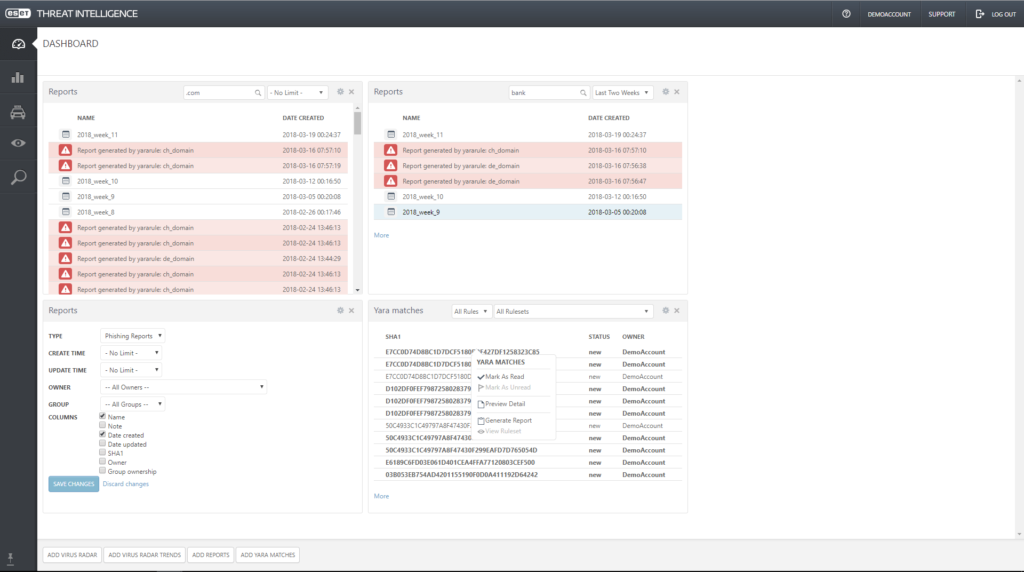
ESET is a threat intelligence platform suitable for businesses of all sizes. It includes multi-vector protection, such as anti-malware, file security, endpoint security, incident response, mail security, and bot protection. Allows users to protect essential information such as usernames and passwords from spyware and viruses by monitoring malicious activities.
ESET threat intelligence platform also enables users to assess the system before installing the program to ensure operational safety.
Key Features:
- Enables users to perform vulnerability assessment into threat sources to create reports
- Available on-premise and web-based
- Enables users to remove malware and spam from email servers
- Provides a mobile app for iOS and Android
To know more about ESET Threat Intelligence Software features and product options, click here to continue.
2. Falcon
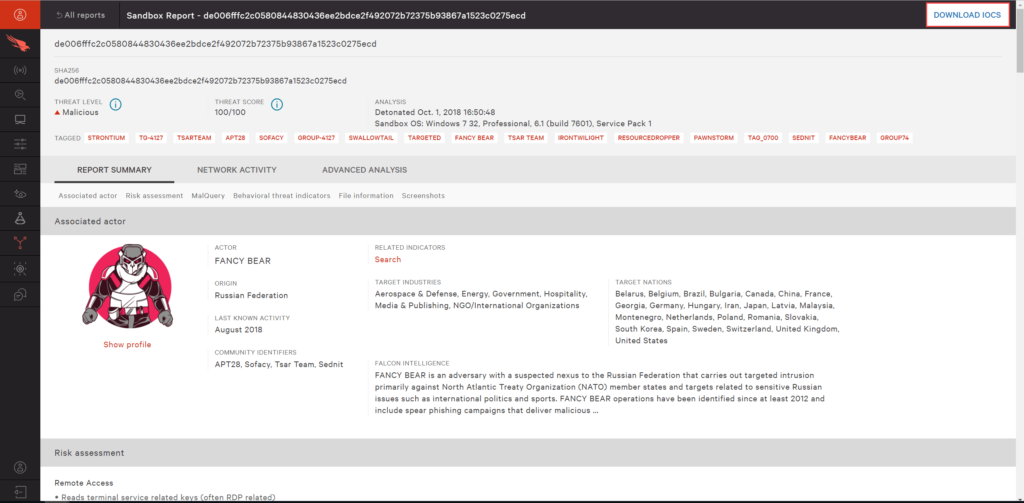
Falcon is a threat intelligence platform designed for businesses of all sizes. Its threat intelligence platform features include advanced threats detection, intelligence data security, preventing various malware activities, AI-based testing, incident response and other security systems features. Allows users to create, manage and change firewall policies. Enables users to track malicious activities and prevent data tampering across various endpoint devices.
Falcon threat intelligence platform also enables users to view and block hackers and prevent unauthorized access in real-time.
Key Features:
- Enables an admin to set permissions and determine access to individuals as per requirements
- Provides a mobile app for iOS and Android
- Allows users to integrate with Cloudflare, Okta, Akamai, Illusive Networks, etc
- Available on-premise and cloud-based
To know more about Falcon Threat Intelligence Software features and product options, click here to continue.
3. Trend Micro
Trend Micro is a threat intelligence platform suitable for the global threat intelligence market. Its threat intelligence platforms features include pre-execution machine learning, data encryption, root cause analysis, etc. Allows users to filter URLs to restrict employees from accessing malicious websites. Enables an admin to track data losses via USB, cloud and email and send alerts or notifications to employees.
Trend Micro threat intelligence platform also allows security analysts to check IP addresses and analyze the website content to track malicious activities.
Key Features:
- Allows users to measure the interruption timeline of vulnerable applications
- Available on-premise and cloud-based
- Trend Micro offers a mobile app for iOS and Android
- Enables users to identify unauthorized website access
To know more about Trend Micro Threat Intelligence Software features and product options, click here to continue.
4. Comodo
Comodo is a threat intelligence platform that can block most cybersecurity threats and malware attacks that steal private data stored on a computer. Also provides free multi-layered protection against malicious behaviour or unknown threats that appear in the form of a suite, integrates Defense+, antivirus protection, and firewalls to achieve full-fledged security against online threats and blocking of advanced attacks.
Comodo threat management provides a Host Intrusion Prevention System’ (HIPS) that allows users to monitor and blocks malicious network intrusions. It provides a mobile app for iOS and Android. Available on-premise and cloud-based. Also provides a desktop app for Mac and Windows.
Key Features:
- Prevents unauthorized modification of critical operating system files and registry entries
- Provides a desktop app for Mac and Windows
- Comodo security management detects & removes rootkits on your computer
- Allows users to detect spyware threats and destroy each infection
To know more about Comodo Threat Intelligence Software features and product options, click here to continue.
5. McAfee
McAfee is one of the most suitable threat intelligence platforms that allows users to identify and blocks vulnerabilities across data centres. Enables users to monitor malicious software or network traffic and prevent attacks. Allows users to connect up to ten devices and protect them from hackers and cybercriminals.
McAfee security solution Windows, Mac, and mobile virus protection, spam filtering capabilities, encryption of sensitive files, dark web protection, etc. Provides a mobile app for ios and Android.
McAfee strategic intelligence allows security analysts to gain visibility into devices and analyze vulnerabilities assessments and endpoint protection. Enables users to integrate with VMware NSX and OpenStack.
Key Features:
- McAfee threat intelligence works as a password manager to manage the password for all your accounts
- Clears your digital footprints regularly and saves your digital identity from attackers
- Provides a complete analysis of your home network, makes your system secure from hackers
- Provides performance optimization for devices, storage and file encryption
To know more about McAfee Threat Intelligence Software features and product options, click here to continue.
6. Vipre
VIPRE is one of the threat intelligence services that provides top-rated malware protection at the best value in the industry. Malicious website and web content blocking. Comprehensive Windows, Mac, and Mobile coverage. Server-based blocking of e-mail-based threats. It provides webcam protection, an device control, network security and security patches for the endpoint.
VIPRE security services protect against Trojans, malicious links, spyware, rootkits, etc. Allows users to schedule scans and monitor current updates. Available on cloud-based and desktop (Mac and Windows operating systems). Also allows users to integrate with existing security systems or existing security tools.
Key Features:
- Monitoring and blocking technology used rule-based and behaviour-monitoring techniques to find rogue apps and shut them down
- Better performance lets you work faster and more efficiently
- VIPRE unified security management provides device control and patch management for an endpoint
- VIPRE Threat Intelligence provides server-based blocking of e-mail-based threats
To know more about Vipre Threat Intelligence Software features and product options, click here to continue.
7. Webroot
Webroot is one of the best threat intelligence solutions that allows users to protect personal information by blocking the latest malware, and cyber-attacks. Also offers simple but powerful antivirus protection, network security, a remarkably flexible backup and file-sharing system, cloud backup and a top-of-the-line password manager.
Webroot threat intelligence solution allows an admin to view scan history, set permission access with a password, and restore isolated files. Users can gain insights into devices and potential malware threats using charts to enhance business processes. Provides a desktop app for Mac and Windows.
Webroot security information management allows users to stop threats across a secure browser, URLs, files, apps, etc. Supports multiple languages, such as French, English, Spanish, etc. Provides a 30-days free trial.
Key Features:
- Provides identity theft protection on mobile devices with a secure browser that blocks malicious websites
- Webroot Threat Intelligence provides Webcam protection
- Protects up to 25GB of digital files from damage or loss with cloud-based backup storage
- Offers secure browsing with real-time anti-phishing
To know more about Webroot Threat Intelligence Software features and product options, click here to continue.
8. Avast
Avast is one of the most suitable threat intelligence platforms that provides 100% protection against zero-day threats. Its threat intelligence capabilities include anti-exploit technology and intelligent antivirus protection that detects viruses, malware detection, ransomware, and a device software updater. It allows users to protect systems from malicious web pages, URLs, files and emails.
Avast threat intelligence enables users to block unapproved access and secure financial transactions or online banking. Enables users to create performance reports in real-time. Provides an app for desktop (Mac and Windows).
Key Features:
- Avast threat intelligence supports (do not disturb mode) can be set for different apps
- Detailed settings for every scan mode
- Available on on-premise and web-based
- Provides Wi-Fi security Secure Password
To know more about Avast Threat Intelligence Software features and product options, click here to continue.
9. Bitdefender
Bitdefender is one of the best threat intelligence platforms that completely covers your PC from all possible threats. Provides the best protection and the lowest impact on performance without compromising speed. Bitdefender threat intelligence provides a secure VPN for complete online privacy.
Bitdefender threat intelligence service allows teams to manage the security of Microsoft Exchange mail servers via the control centre console using anti-spam and anti-malware functionality. It allows users to share threat intelligence and provides network protection and the protection of mobile devices across various locations. Allows users to connect up to five devices.
Key Features:
- Provides multi-layer ransomware protection to keep your files safe
- Innovative technologies to protect against zero-day attacks
- Unbeatable threat database detection to stop sophisticated malware
- Advanced parental controls to keep your kids safe online
To know more about Bitdefender Threat Intelligence Software features and product options, click here to continue.
10. Symantec

Symantec is a threat intelligence service suitable for small to mid-sized businesses. Its threat intelligence capabilities include antispyware, firewall, anti-malware, etc. Allows security analysts to analyze applications and files and protect them from possible threats. Enables an admin to set rules for users and devices. Symantec actionable intelligence provides automatic updates to keep the systems’ security up-to-date.
Key Features:
- Symantec threat intelligence allows users to receive alerts via email and SMS
- Available on-premise and web-based
- Provides a mobile app for iOS and Android
- Provides a desktop app for Mac and Windows
To know more about Symantec Threat Intelligence Software features and product options, click here to continue.
11. SentinelOne
SentinelOne is one of the real-time threat intelligence platforms suitable for businesses of all sizes. It includes whitelisting or blacklisting, activity log management, behavioural analytics, etc. Enables users to identify and fix threats across systems, including mobile devices. SentinelOne actionable intelligence allows users to scan and detect multiple threats, such as trojans, worms, and malware. Provides a mobile app for iOS and Android.
Key Features:
- Enables users to gain insights into system performance in real-time
- Provides a desktop app for Mac and Windows
- Allows users to integrate with Okta, Splunk, Fortinet, etc
- Available on-premise and cloud-based
To know more about SentinelOne Threat Intelligence Software features and product options, click here to continue.
12. Infocyte
Infocyte is a cloud-based threat intelligence software suitable for businesses of all sizes. It includes validation of security operations controls, live-memory analysis, post-incident certifications, etc. Allows users to identify, track and fix cyber threats using machine learning.
Infocyte security vendors allow an admin to monitor scanned and unscanned operating systems. Enables users to track various malicious activities across cloud architectures or data centres.
Key Features:
- Provides compliance management, such as the Center for Internet Security (CIS)
- Infocyte security solutions work on Mac, Windows and Linux
- Allows users to integrate with Swimlane, ForeScout, ForeScout, etc
- Provides a free trial with limited features
To know more about Infocyte Threat Intelligence Software features and product options, click here to continue.
13. Kaspersky
Kaspersky is one of the most suitable threat intelligence platforms for small to mid-size businesses. It includes encryption management, firewalls, threat intelligence sharing, mobile threat defence, anti-phishing, anti-spam protection, etc. Allows users to detect malware and emerging threats and fix them. Enables users to gain insights into global threats in real-time.
Kaspersky threat intelligence services allow users to integrate with SIEM and EMM applications. Enables an admin to set permissions and determine access to their team members as per requirements.
Key Features:
- Available on-premise and cloud-based
- Kaspersky security solutions work on Windows, Mac and Linux
- Provides a mobile app for iOS and Android
- Also provides a free trial
To know more about Kaspersky Threat Intelligence Software features and product options, click here to continue.
14. IntSights
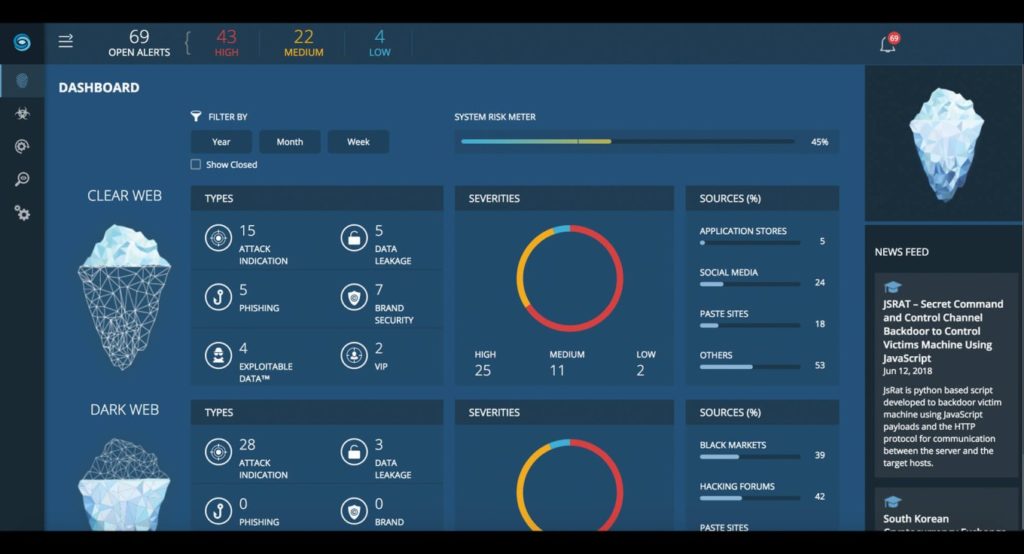
IntSights is one of the most suitable cloud-based threat intelligence platforms designed for businesses of all sizes. It includes threat hunting, dark web monitoring, vulnerability management, etc. Allows users to detect malware and phishing attempts and fix them across the web. Enables users to monitor and identify data leakages or threat hunting and set alerts based on historical threat attacks.
IntSights threat intelligence allows users to combine threats intelligence data from multiple sources on a unified dashboard and enables an admin to scan against malicious assets. Allows users to configure alerts in real-time using machine learning algorithms.
Key Features:
- IntSights provides a browser extension
- Provides compliance management, including GDPR, HIPAA, PCI DSS, and NERC CIP
- Allows users to integrate McAfee, Forcepoint, Fortinet, Micro Focus, etc
- Supports multiple languages, such as French, English, Spanish, etc
To know more about IntSights Threat Intelligence Software features and product options, click here to continue.
15. AlienVault USM Anywhere
AlienVault USM Anywhere is one of the best threat intelligence platforms suitable for businesses of all sizes. It includes security breaches monitoring, threat analysis, vulnerability assessment, host intrusion detection, risk detection, and cyber threat response. Allows users to obtain and detect information, such as the number of logged-in users, the operating system of assets, etc.
AlienVault USM Anywhere combines threat intelligence and provides pre-built event reporting templates, customizable dashboards and dark web monitoring. Allows users to gain visibility into system performance.
Key Features:
- AlienVault threat intelligence feed tool allows users to integrate with Office 365, Jira, Palo Alto Networks, etc
- Provides a desktop app for Windows
- AlienVault unified security management provides a free trial
- Available on-premise and cloud-based
To know more about AlienVault USM Anywhere Threat Intelligence Software features and product options, click here to continue.
Conclusion
Threat Intelligence Platform provides an effective and secure method for protecting your combined threat intelligence data using machine learning and artificial intelligence. Detected applications analyze the code generated from any new program against the signature found on the data from the previous detection. These tools could analyze the attack signatures of the potential threats and transmit these data back onto other systems.
Frequently Asked Questions
What Are Threat Intelligence Feeds?
Threat Intelligence feeds high-level analysis for users with less technical knowledge. It comes from open sources, including national and local media and white papers. Also comes from analysing the details of past threat attacks.
Is Alienvault Ossim an Open-Source Tool for Threat Intelligence?
AlienVault OSSIM is an open-source security information and event management software. It gathers event data from multiple security systems logs, such as operating systems and applications and enterprise security operations controls, cloud infrastructure monitoring, and log management.
What Is Solarwinds Event Security Manager?
Solarwinds security event management integrates events that have been tracked across your network with a Proofpoint emerging threat and analysis in the background from external sources. The solution offers tools designed to log data from all sources. The software helps you monitor network activity, look up unusual events, and keep an eye on essential files.
Log Analysis in SEM collects logs from incompatible sources asynchronously and returns these logs to neural networks. The analytical device can analyze an activity pattern based on a single equipment configuration across multiple systems and not just a specific one.
What Are the Three Types of Adaptive Threat Detection?
Strategic Cyber Threat Intelligence: It allows users to find the reasons and attackers behind specific threats. It can be created in briefings, reports and white papers.
Tactical Cyber Threat Intelligence: It allows users to find where and how the attack occurs. Enables users to prevent threats based on historical data. Also provides strategies and methods to better understand and respond to threats.
Operational Threat Intelligence: Its indicators are obtained from attacks performed against data and active campaigns. It can be created in file names, IP addresses, domain names, URLs, etc. Allows users to monitor and block attacks within a network.
What Is the Best Threat Intelligence Software?
1) Falcon threat detection allows government agencies to create, manage and change firewall policies. Enables users to track malicious activities and prevent data tampering across various endpoint devices. Also enables users to view and block hackers and prevent unauthorized access in real-time.
2) AlienVault USM Anywhere threat detection allows users to obtain and detect information, such as the number of logged-in users, the operating system of assets, etc. AlienVault unified security management nables users to gain visibility into system performance.
3) McAfee threat detection enables users to monitor malicious software or network traffic and prevent attacks. Allows users to connect up to ten devices and protect them from hackers and cybercriminals. It enables an admin to gain visibility into devices and analyze vulnerabilities assessments and endpoint protection.
4) Kaspersky threat detection allows users to detect malware and emerging hidden threats and fix them. Also enables users to integrate with SIEM and EMM applications.
5) IntSights global threat data feeds detection allows users to combine data from multiple sources on a unified dashboard and enables an admin to scan against malicious assets. Enables users to monitor and identify data leakages and set alerts based on historical threat attacks.
6) VIPRE threat data detection protects against Trojans, infected attachments, malicious links, spyware, rootkits, etc. It provides Monitoring and blocking technology that uses rule-based and behaviour monitoring techniques to find rogue apps and shut them down.
Is Trend Mirco Threat Data Detection a Good Security Threats Software?
Trend Micro threat data detection enables an admin to track data losses via USB, cloud and email and send alerts or notifications to employees. It allows users to measure the interruption timeline of vulnerable applications.
What Are the Three Elements of Cybersecurity?
1) Confidentiality: It means that the data is stored confidentially and cannot be accessible by all users. It allows only authorized users to access confidential data.
2) Integrity: It means the certainty that the data is not degraded intentionally or unintentionally when transferring, uploading, and storing data.
3) Availability: It means information is available to authorized users when required for a system to verify. It must have adequately functioning security controls and computing systems.



