In today’s dynamic business environment, risks are limitless, but resources like time and budget are not. Prioritizing risks is essential to efficiently address potential threats. Cyber risk prioritization is a systematic process of evaluating risks, assessing their likelihood, and determining their impact to decide which should be mitigated first. Let’s explore how cyber risk prioritization works, what factors should be considered, and how Governance, Risk, and Compliance (GRC) technology can streamline the process for better outcomes.
What is Risk-Based Prioritization?
Risk-based prioritization involves ranking risks based on their potential severity and likelihood of occurrence. By focusing on the risks most critical to your organization, you can allocate resources where they are most needed. For example, while an earthquake might pose a severe threat, it could be a low-priority risk if your location has no history of seismic activity. On the other hand, if your data centres are a critical asset, the likelihood of a cyberattack could be high, necessitating immediate attention.
The goal is to establish a rank-order system from most critical to least critical risks. This approach ensures efficient allocation of resources, linking risk mitigation efforts to key business objectives.
Levels of Risk Prioritization
Risk prioritization typically falls into five categories, each reflecting the severity and likelihood of impact:
- Tolerable Risk: Risks with minimal chance of harm or impact.
- Low Risk: Minor risks with low probability and limited negative consequences.
- Medium Risk: Risks that may not pose immediate threats but can still cause considerable damage.
- High Risk: Critical risks that could significantly disrupt projects or operations.
- Intolerable Risk: Catastrophic risks could lead to major system failures, necessitating immediate action to prevent severe loss.
Using a risk prioritization matrix, you can assess the likelihood and impact of potential risks visually, simplifying the decision-making process for addressing them.
An example of a simple risk matrix:
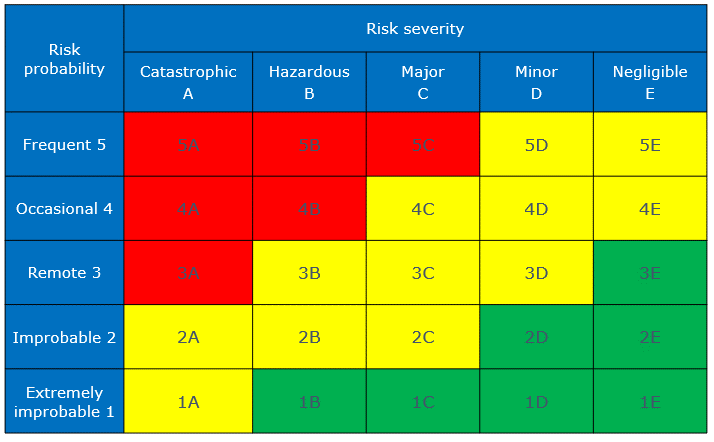
Key Types of Cyber Risks
The risks facing organizations today can be broadly classified into five main categories:
Cybersecurity Risks
- Cybersecurity risks range from ransomware, phishing, and data breaches to insider threats and physical security concerns. These risks can result in operational, financial, and reputational damage. Prioritizing vendor and supply chain risks is essential, as third-party vulnerabilities can impact your security posture. Automation can significantly enhance the efficiency of identifying and prioritizing these risks by reducing manual effort.
User and Functionality Risks
- These risks revolve around how users interact with your product or service. This includes factors like user access control, web application security, and adoption rates. Properly managing these risks ensures that systems remain secure while meeting user needs.
Control Risks
- Control risks arise when internal security measures fail. It is crucial to regularly monitor, test, and assess these controls to ensure they continue functioning as expected. Regular updates and evaluations based on their importance can prevent control failures.
Performance Risks
- These risks pertain to the overall functionality and efficiency of a product or service. Poor implementation, lack of maintenance, inadequate training, and changes in demand can contribute to performance risks. Continuous monitoring and prompt remediation plans can help mitigate these risks.
System Architecture Risks
- System architecture risks are associated with vulnerabilities in the design of your IT infrastructure. As organizations add new technologies or users to their networks, the risk of introducing vulnerabilities increases. Assessing these risks is key to ensuring that the IT landscape remains resilient to evolving threats.
Key Components of Risk-Based Prioritization
Risk Identification
- The first step is to identify potential risks that may affect an organization’s goals. This can include everything from operational risks (like supply chain disruptions) to strategic risks (such as market changes) and compliance risks (related to regulatory requirements).
Risk Assessment
- Once risks are identified, they are assessed based on two main criteria:
- Likelihood: The probability of a risk occurring. This can be informed by historical data, industry trends, or expert judgment.
- Impact: The potential consequences of the risk if it were to materialize, which can range from minor inconveniences to catastrophic failures.
Risk Ranking
- After assessment, risks are ranked in a risk register or matrix format, often visualized in a grid where one axis represents likelihood and the other represents impact. This ranking helps decision-makers quickly see which risks require immediate attention.
Resource Allocation
- Prioritizing risks allows organizations to allocate resources more effectively. High-priority risks, which are both likely to occur and have a significant impact, receive immediate attention and funding for mitigation strategies, while lower-priority risks may be monitored or addressed later.
Continuous Monitoring and Review
- Risk-based prioritization is not a one-time activity. It should be a continuous process, with regular reviews and updates based on changes in the organization’s environment, new risks that emerge, or shifts in business strategy. This ensures that the prioritization remains relevant and effective.
Benefits of Risk-Based Prioritization
Enhanced Decision-Making
- By providing a clear picture of risks, decision-makers can focus on what matters most to the organization, leading to more informed choices.
Optimized Resource Utilization
- With limited time and budgets, prioritizing risks helps ensure that resources are directed where they can have the greatest impact, improving overall efficiency.
Improved Risk Management
- By focusing on high-priority risks, organizations can reduce their vulnerability to potential threats, ultimately leading to stronger risk management practices.
Alignment with Business Objectives
- Risk-based prioritization ensures that risk management activities are aligned with the organization’s mission and objectives, supporting strategic goals rather than hindering them.
The Role of GRC Technology in Risk Prioritization
Modern GRC platforms offer powerful solutions for managing cyber risk prioritization. Automated tools can conduct thorough risk assessments, map risks to industry standards, and recommend mitigation steps. GRC solutions help organizations automate the evaluation of risk impact and likelihood, saving time and reducing human error.
Platforms like Centraleyes provide cutting-edge tools for risk assessment, allowing businesses to convert technical risks into business risks. This holistic approach includes vendor risk management, ensuring complete oversight of all potential vulnerabilities. These tools also generate customized risk reports, simplifying the decision-making process.
By leveraging GRC technology, organizations can ensure that risks are systematically identified, ranked, and mitigated, optimizing resource allocation and improving overall security posture.



